Securing Digital Files with an Electronic Document Management System
Securing Digital Files With an Electronic Document Management System
Securing important digital files with an electronic document management system creates an environment in which workers can collaborate across locations while staying organized and maintaining secure control over critical intellectual property assets while accessing their files and documents remotely.
Secure access is paramount when managing confidential files, as proprietary drawings and documents are at risk of theft by nefarious criminals, competing organizations, and other bad actors. Fortunately, there are several methodologies organizations can use to ensure they are securing important digital files and documents are kept safe within the system and only accessible by permitted users.
Some of the ways organizations secure their files include:
Multifactor authentication
Multifactor authentication (aka,. two-factor authentication) is a security technology that requires users to use multiple methods of authentication from several categories of credentials. It utilizes a combination of factors, including passwords, biometric verification, or security tokens.
The most common form of multifactor authentication is Google’s 2-Step Verification, which provides users with a unique, time-sensitive password that changes every minute. This requires users to have a security key, often provided on a user-specific device.
Multifactor authentication provides excellent protection against brute-force attacks, in which attackers try various passwords and usernames to eventually make their way into the system. These attacks are often automated, allowing attackers to try thousands, if not millions, of password combinations to gain access to the system.
Limiting login attempts
As an additional measure, EDMS admins can limit the number of logins attempts from a single device. This further reduces the risk of a brute-force attack, as the attacker will have a limited number of chances to guess the password. Combine this with additional two-step verification, and the attacker will have little to no opportunity to gain access to the system.
IP whitelisting
Attackers from all over the world will often try to access the system, so organizations need to limit access to the system based on the geographic location of each user. IP Whitelisting allows users from administrator-approved locations to gain access to the system while restricting people in unapproved locations from attempting to login to the system.
IP Whitelisting is an aspect of multifactor authentication, perfect for organizations that only want users to access the system from a specific geographic location. It's great for in-office employees and companies that operate on a regional scale.
System access control
Since not all workers carry the same responsibilities, some workers need to be granted access to certain projects within the document management system, without having access to all the files within the system. Access control enables organizations to access files that are pertinent to their role, without granting them access to the remainder of the files within the system or to functionality related to files, such as downloading and printing.
With ImageSite, system administrators can define users based on their roles and responsibilities, and provide them with access to the specific projects, folders, or files. Additionally, system admins can control access at the file metadata level, making it easier for them to provide access to files per role.
Additional EDMS Features
Our EDMS solutions
ImageSite and EngineBox are eQuorum’s robust workflow and document management solutions, created to help workers manage their essential workflows while maintaining complete control over their engineering files and documents. Not only do they provide a secure collaboration site for workers, but they also help organizations manage document distribution with third parties like vendors, contractors, and customers. Both systems are offered at a competitive price, enabling organizations to get a quick return on their investment by providing the features and functionality needed to help organizations improve efficiency, productivity, and collaboration. Companies can choose from concurrent user subscriptions or named user subscriptions, ensuring organizations have subscription options that make sense for their business.
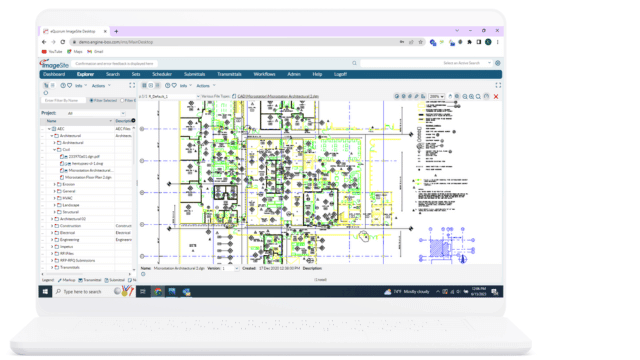
ImageSite®
Our single source engineering workflow and document management system. Built in HTML5 so there is no software to deploy to client computers or mobile apps to download. Offered as an On-premise or Private Cloud system.
EngineBox™
EngineBox is a cloud based workflow and document management version of ImageSite that resides outside the corporate network.
Our EDMS solutions
ImageSite and EngineBox are eQuorum’s robust workflow and document management solutions, created to help workers manage their essential workflows while maintaining complete control over their engineering files and documents. Not only do they provide a secure collaboration site for workers, but they also help organizations manage document distribution with third parties like vendors, contractors, and customers. Both systems are offered at a competitive price, enabling organizations to get a quick return on their investment by providing the features and functionality needed to help organizations improve efficiency, productivity, and collaboration. Companies can choose from concurrent user subscriptions or named user subscriptions, ensuring organizations have subscription options that make sense for their business.
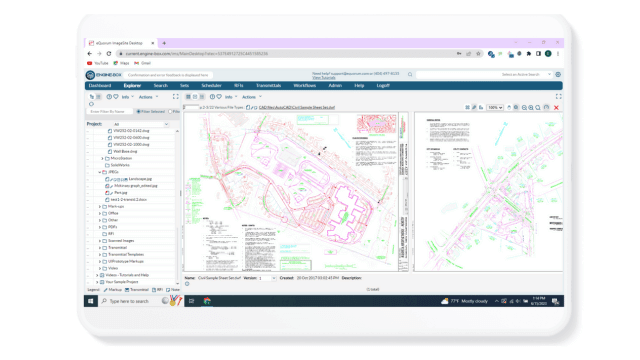
EngineBox™
EngineBox is a cloud based workflow and document management version of ImageSite that resides outside the corporate network.
The eQuorum Customer Promise
In 2005, eQuorum developed the first all browser-based EDMS. The system, although for on-premise use, was still created to remove client software and JAVA from user computers and allow users to have a single viewer based on the simple navigation functionality of browsers. Today, eQuorum provides that same application in a private Cloud or a SaaS Cloud option. We can do this because we are, and have always been, browser-based, understanding the enhanced speed, security, and usability of this technology.
With the abundance of document management systems on the market today, there’s no doubt that choosing the right Cloud document management software can be a difficult decision. eQuorum is here to provide a comprehensive, powerful, and most importantly – affordable Cloud document management solution. We believe in providing real value to our customers by eliminating unnecessary costs, providing industry-leading functionality, and equipping your team with the right tools using cutting edge technology to bring your products to market faster.
eQuorum®
We specialize in engineering workflow and document management. Our comprehensive, yet easy-to-use software provides the solution to manage data from design to manufacturing and production, to sales, support and administration.